I’m delighted to announce (official version) that my team at Dell has opened the Crowbar source under the Apache 2 license. This action is part of the broader Dell OpenStack Cloud Solution which includes OpenStack install packages, Crowbar, reference hardware architectures, and services/consulting to support deployments.
I’m delighted to announce (official version) that my team at Dell has opened the Crowbar source under the Apache 2 license. This action is part of the broader Dell OpenStack Cloud Solution which includes OpenStack install packages, Crowbar, reference hardware architectures, and services/consulting to support deployments.
There are two important components to this news:
- Dell is officially offering our OpenStack Solution and helping advance the community’s ability to implement OpenStack quickly and consistently.
- Dell is releasing the Crowbar code (which is included in the solution) as open source.
Both are significant items; however, my focus here is on the Crowbar release.
Crowbar started as a Dell OpenStack installer project and then grew beyond that in scope. Now it can be extended to work with other vendors’ kits and other solutions bits.
We are contributing Crowbar to the community because we believe that everyone benefits by sharing in the operational practices that Crowbar embodies. These are rooted in Opscsode Chef (which Crowbar tightly integrates with) and the cloud & hyper-scale proven DevOps practices that are reflected in our deployment model.
Where to get it?
- Code: Github (Apache 2 license)
- Community: Dell Crowbar listserv,
- Information: wiki on Crowbar Github, Crowbar User’s Guide and RobHirschfeld.com web site.
What’s included?
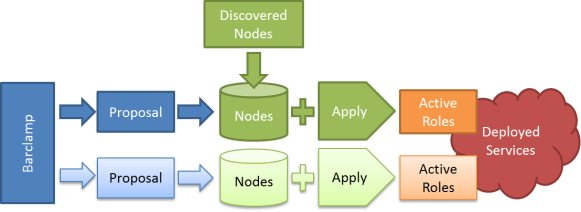
- A comprehensive set of barclamps to set up an OpenStack cloud.
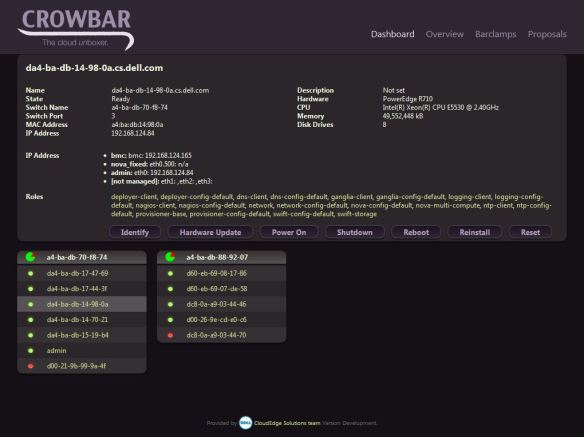
- Crowbar UI and Remote APIs to make it easy to set up your cloud
- Automated testing scripts for community members doing continuous integration with OpenStack.
- Build scripts so you can create your own Crowbar install ISO
- Switch discovery so you can create Chef Cookbooks that are network aware.
- Open source Chef server that powers much of Crowar’s functionality
What’s not included?
- Non-open source license components (BIOS+RAID config) that we could not distribute under the Apache 2 license. We are working to address this and include them in our release. They are available in the Dell Licensed version of Crowbar.
- Dell Branded Components (skin + overview page). Crowbar has an OpenSource skin with identical functionality.
- Pre-built ISOs with install images (you must download the open source components yourself, we cannot redistribute them to you as a package)
Important notes:
- Crowbar uses Chef Server as its database and relies on cookbooks for node deployments. It is installed (using Chef Solo) automatically as part of the Crowbar install.
- Crowbar has a modular architecture so individual components can be removed, extended, and added. These components are known individually as barclamps.
- Each barclamp has its own Chef configuration, UI sub-component, deployment configuration, and documentation.
On the project roadmap:
- Hadoop support
- Additional operating system support (specifically RHEL)
- Barclamp version repository
- Network configuration
- We’d like suggestions! Please comment!
Sites for more information: Joseph George, Barton George (launch day), Dell

 Original Post
Original Post