10/18 Update:
More recent information about Barclamps can be found at https://robhirschfeld.com/2011/09/14/details-of-crowbar-changes/. We’ve also created videos showing how you can create your own barclamps.
 Original Post
Original Post
Just after we’d started deep Crowbar development, Andi Abes, Paul Webster and Victor Lowther joined the Dell Crowbar+OpenStack team. They immediately started to dig into our Swift, BIOS/RAID, and Network components. They also started to bump into each other in our original code base. It quickly became apparent that we needed to modularize Crowbar.
Restructuring Crowbar into modules has proved essential as a method for safe community collaboration.
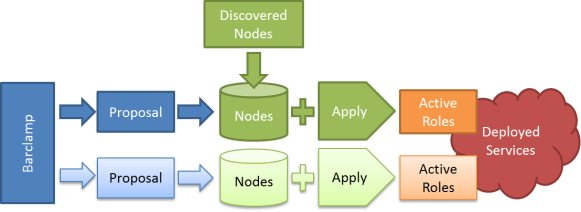
Greg Althaus coined the name “barclamps” during the modularization rearchitecture. A barclamp is a class extension of the Crowbar ServiceObject that allows Crowbar to identify the Chef components used by the barclam
p (name p
attern in Chef is bc-template-[barclamp]) and provides capabilities that are specific to each barclamp.
- In the simplest case, the barclamp is a minimal wrapper that just provides naming hooks for your Chef cookbooks. This makes it very easily to adapt existing Chef work to work with Crowbar.
- In more complex cases, the barclamp will help identity how nodes are allocated, interacts with other barclamps, extends the provisioner state machine and provides custom user interfaces.
- In most cases, the barclamp’s generic integration and UI are sufficient.
When looking at the barclamps, it is critical to understand that even the most core Crowbar functionality is expressed as a barclamp.
- helps modularize the code and
- reflects the deep integration between Chef and Crowbar.
Consequently, the core logic of the state machine, networking configuration, and provisioning are all exposed in barclamps. This makes it possible to modify and extend the most basic Crowbar operations; however, there are currently no guards against breaking these barclamps either!
| Barclamp | Function | Included |
| Crowbar | The roles and recipes to set up the barclamp framework. | Yes |
| Deployer | Initial classification system for the Crowbar environment (aka the state machine) | Yes |
| Provisioner | The roles and recipes to set up the provisioning server and a base environment for all nodes | Yes |
| Network | Instantiates network interfaces on the crowbar managed systems. Also manages the address pool. | Yes |
| NTP | Common NTP service for the cluster. An NTP server or servers can be specified and all other nodes will be clients of them. | Yes |
| DNS | manages the DNS subsystem for the cluste | Yes |
| Logging | centralized logging system based on syslog | Yes |
| IPMI | Integrates with IP management to allow direct hardware control bypassing the operating system. | Yes |
| RAID | LSI Licensed components. Cannot be included in open source release at this time. | No |
| BIOS |
PowerEdge C series: Dell License component. Cannot be included in open source release at this time. | No |
| Ganglia | Optional: a common Ganglia service for the cluster that can be used by other barclamps | Yes |
| Nagios | Optional : common monitoring service for the cluster that can be used by other barclamps | Yes |
| Nova | OpenStack: installs and configures the Openstack Nova (Cactus Release) component. It relies upon the network and glance barclamps for normal operation. | Yes |
| Swift | OpenStack: part of Openstack (Cactus Release) , and provides a distributed blob storage | Yes |
| Glance | OpenStack: Glance service (Cactus Release, Nova image management) for the cloud | Yes |
| Test | provides a shell for writing tests against | Yes |